C11: The Impact of Computing
I went to my first computer conference at the New York Hilton about 20 years ago. When somebody there predicted the market for microprocessors would eventually be in the millions, someone else said, "Where are they all going to go? It's not like you need a computer in every doorknob!" Years later, I went back to the same hotel. I noticed the room keys had been replaced by electronic cards you slide into slots in the doors. There was a computer in every doorknob. — Danny Hillis (circa 1999)
Technology is, of course, a double edged sword. Fire can cook our food but also burn us. — Jason Silva
Computers have changed our society over the last 80 years — helping to end wars, creating tools that have led to advances in medicine, making jobs safer, placing vast amounts of knowledge at our fingertips, and enabling people to connect in ways that would have been unthinkable just a few decades ago. Overall, the changes brought about by computer technology have been extremely positive, and it is difficult to imagine a society that is not connected and tech-pervasive. But not all change is good, and like any tool, computers can be used to harm as well as help. Many people are becoming dependent on technology, often to the detriment of personal relationships. Online activities and credit card purchases can be used to collect information on many aspects of a person's private life. The same technology that automates dangerous or tedious tasks can cost workers their jobs.
Hopefully, reading this book has helped you to better understand computer technology — where it came from, how it works, and how difficult it is to get it perfect. This deeper understanding should guide you as you make choices about how to adopt technology in your life, and how to balance the benefits and the dangers that computer technology presents.
Technology and Society
In 2024, WT Wealth Management published a white paper written by John Hellner. This paper, titled 10 Inventions that Have Changed the World, identified and ranked "ten of the most impactful inventions that have changed the world." Although any such list leaves room for debate, there is no doubt that the inventions listed by Hellner (FIGURE 1) have influenced the way in which society is structured. For example, the printing press allowed for knowledge to be preserved and shared, leading to widespread literacy and scientific advancement. The availability of telephone service contributed to the decentralization of society, in that phones enabled people to communicate and conduct business over large distances. The automobile changed the face of society by increasing personal mobility. When people obtained their own affordable mode of transportation, they were able to move away from urban areas and still drive to their jobs, which led to suburbanization and the rise of today's "commuter culture." It is interesting to note that the last four entries in his list are computing innovations, (7) the personal computer, (8) the Internet, (9) the mobile phone, and (10) artificial intelligence.
| Top 10 Inventions |
|---|
|
FIGURE 1. 10 Inventions that have Changed the World. (John Hellner)
Computing technologies are still evolving, which means that they continue to impact society in new ways. The personal computer revolution of the late 1970s and early 1980s put computers in the hands of individuals. The Internet changed the ways in which we communicate and drives today's information-based economy. The mobile phone, especially the smart phone, has put the power of communication and information processing in the hands of individuals on the move. Artificial Intelligence is changing the way we write, create, and access information. As computer scientists continue to augment existing technologies and develop new applications, the potential for computer technology to influence daily life appears unlimited.
FIGURE 2 shows an interesting comparison of technology adoptions over the last century. Note that the three early inventions listed (electric power, radio and the automobile) were adopted slowly over time. For example, the automobile required 55 years to reach 80% of American households. In contrast, the various computer-related technologies were adopted at highly accelerated rates. For example, the personal computer grew from 20% to 80% of U.S. households in 21 years; the cell phone grew from 10% to 84% of households in 15 years; the smartphone grew from 35% to 81% of households in just 8 years.
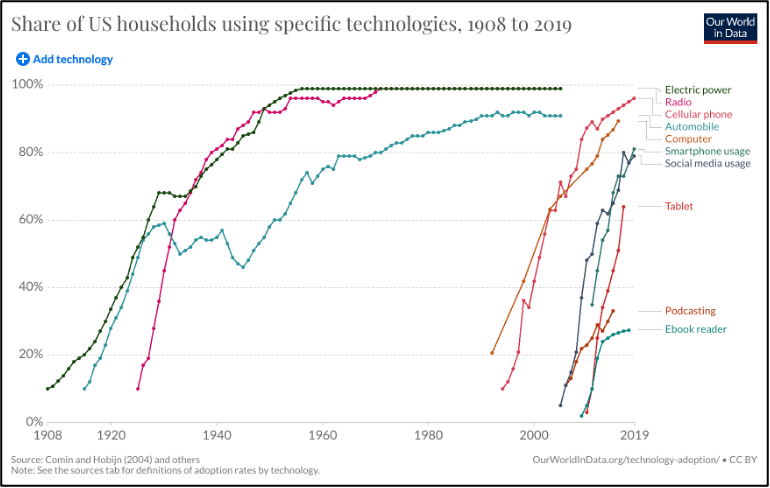
FIGURE 2. Adoption rates of various technologies. (OurWorldInData.org, 2019).
✔ QUICK-CHECK 11.1: Do you think that Hellner's list (FIGURE 1) represents the 10 most important and/or impactful inventions? If not, what inventions do you think are missing from this list? What possible developments in computer technology might increase the relative importance of computers?
Digital Banking
One obvious example of the computer's impact on society is the changing nature of money. As recently as 50 years ago, the United States was largely a cash-based society. Workers were paid with paper checks, which they would take to their local bank and exchange for cash. Most purchases were made with cash or check. Banks made agreements to cash each other's checks, but each check required a physical transfer of cash between the banks to maintain balance.
Two developments in the 1980s changed the way we view money. First, the development of microprocessors led to devices for scanning and processing transactions. These made credit cards more convenient for customers and cost-effective for retailers. When combined with government deregulation, these advances led to nationwide service networks and the widespread adoption of credit cards. Second, the growth of the Internet enabled banks to communicate and transfer funds seamlessly. Banks discovered that the transfer of physical money was often unnecessary. Instead, transfers could be done electronically over the network, essentially replacing cash with electronic IOUs between the banks. If the accounts became too unbalanced, then the banks could still transfer cash, but for the most part they just treated money as numbers in files. Automated Teller Machines (ATMs), which had been around since the late 1960s, exploded as a result of this development. A customer could go to any bank's ATM, regardless of location, and withdraw cash. The transaction would be shared across the network with both the ATM's bank and the customer's bank and the electronic transfer of funds between those banks would be recorded. As a result, debit cards that could be used to access ATMs and make purchases linked to bank accounts also grew in popularity in the 1980s.
Because of the widespread availability of credit/debit card scanners and ATMs, people can now access their money around the clock from almost any location (FIGURE 3). As a result, they are no longer dependent on cash reserves to purchase goods. From pay-at-the-pump gas stations to vending machines with credit card readers, computing technology makes it easier for customers to make cashless purchases. A 2024 survey conducted by DepositAccounts found that 61% of respondents made five or fewer cash purchases in the previous month, 66% don't always carry cash, and 73% typically carry $50 or less. CapitalOne estimated a total of 56.2 billion domestic credit card transactions in 2024, with the worldwide total surpassing 791 billion.


FIGURE 3. ATMs and debit-card readers allow consumers to access cash or pay directly in stores.
Another factor in the move away from cash is online banking. Most banks provide Web sites where customers can transfer funds or make payments without needing checks or even access to a bank branch. Most banks provide apps that enable customers to take a snapshot of a check and deposit it directly into their account. Similarly, employees can have their paychecks directly deposited to a bank account and schedule automatic bank transfers to pay monthly bills.
The past decade has seen the introduction of cryptocurrencies, entirely electronic forms of money that are not backed by any government or financial institution. Instead, the value of a cryptocurrency such as Bitcoin or Ethereum is entirely determined by the free market. Investors can trade crypto-coins the same as stock investments, and their value fluctuates based on consumer demand and acceptance by retail outlets. Cryptocurrencies rely heavily on advanced encryption algorithms (Chapter C7) for security and offer advantages with respect to privacy (including truly anonymous purchasing). However, they can also be extremely speculative, with value fluctuating wildly based on market demand. At this early stage, it is not clear whether cryptocurrencies will become serious alternatives to traditional currencies or will instead be viewed as a temporary fad.
 Crypto Risk
Crypto Risk
It is important to realize that cryptocurrencies are not like other, more established forms of currency. Cash is backed by the government, ensuring that it will retain value as long as the government is sound and fiscal policies are followed. When you deposit money in a bank, the Federal Deposit Insurance Corporation (FDIC) insures that money (up to $250,000) from loss. In contrast, there are no guarantees with cryptocurrencies. Since the value of a cryptocurrency is entirely dependent on what people agree it is worth, they can be extremely volatile. A good example is an incident in 2021, when Elon Musk appeared on Saturday Night Live and made a joke about Dogecoin. As a result, its value dropped 44% overnight! CoinGecko, a firm that tracks and analyzes cryptocurrencies, reported that over 50% of cryptocurrencies failed, with more than 1.8 million failures in 2025 alone.
Another risk of cryptocurrencies is derived from their anonymity. Cryptocurrency purchases can be performed anonymously, with the purchaser receiving a passcode that provides access to their coins. If that passcode is lost, there is no way for them to prove that they are the owner, and those coins are just lost. This happened to James Howells from Newport City, Wales. In 2013, he accidentally threw away his computer that stored his passcode for bitcoins, which are now worth more than $800 million dollars. After later realizing his mistake, he approached the city council for permission to search the local landfill but was denied because of the negative environmental impact it would cause. As of 2025, he has still not been able to search the landfill and is hoping to buy it from the city.
✔ QUICK-CHECK 11.2: TRUE or FALSE? Computer technology has greatly impacted the banking industry, to the extent that credit cards and debit cards have reduced consumers' reliance on cash.
Debt and Online Theft
As with most technologies, the advantages of electronic alternatives to cash also bring the potential for abuse or negative consequences. Since most people always carry a debit/credit card with them, the opportunity to spend is constant. Studies have shown that people spend more freely when using a credit or debit card as opposed to cash. Credit card interest rates are the highest for any type of debt, making it all too easy for consumers to become buried in debt. For example, the average credit card interest rate as of July 2025 was 22.25% (U.S. Federal Reserve Board). In contrast, the average interest rate for a 30-year fixed-rate mortgage was 6.24% (Freddie Mac) and the interest earned on a 5-year CD (certificate of deposit) was only 1.69% (BankRate).
Credit card debt continues to be a major concern for many consumers, especially in the U.S. where credit cards are widely used because of their convenience. In November 2025, the Federal Bank of New York estimated the total U.S. credit card debt to be $1.23 trillion, for an average of $9,276 per household. For many families, credit card debt exceeds their savings, leading to a spiral in which they can only make a minimal payment each month and the interest continues to accumulate.
Interestingly, the shift from physical to electronic money has had both positive and negative impacts on crime. With people carrying less cash, muggings in the U.S. have decreased steadily in recent decades. However, physical theft has been replaced by new forms of robbery. Identity theft is a relatively new crime in which the thief steals personal information (e.g., credit/debit card numbers or ATM passwords) and poses as the legitimate cardholder to extract cash or make purchases (FIGURE 4). The U.S. Federal Trade Commission reported 1.1 million cases of identity theft in 2024, with a total loss of over $12.7 billion. Fortunately, the risk to consumers is mitigated by bank and credit card company policies that do not hold the cardholder responsible for fraudulent purchases. If a credit card customer notes a fraudulent charge on their bill, they can report it to the credit card company and are no longer responsible for that charge. Shifting the costs of fraud away from the consumer costs companies in the short term. However, the confidence that consumers experience due to their lack of risk leads to increased spending and greater profits for the company in the long term.
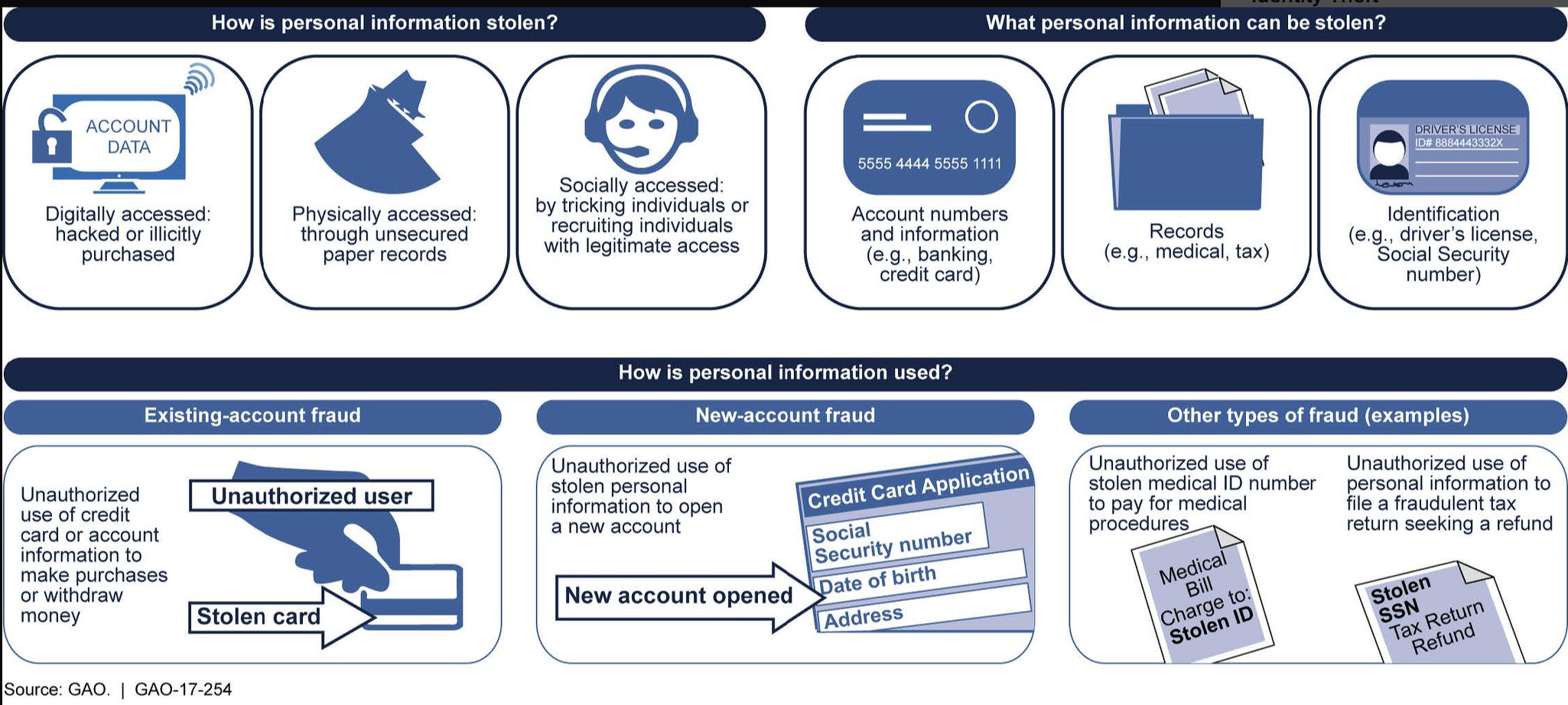
FIGURE 4. Examples of identity theft and fraud (U.S. Government Accountability Office).
✔ QUICK-CHECK 11.3: TRUE or FALSE? Credit card interest rates are comparable to other loan rates, such as mortgages.
Computers and Software for Everyday Tasks
Although ATMs and debit/credit card readers serve as visible reminders of our reliance on technology, modern life also depends on thousands of less obvious, hidden computer applications. Embedded processors, computer chips built into appliances and machinery to control their workings, account for 98% of all computer processors manufactured. Modern houses contain hundreds of embedded processors, concealed in devices such as microwave ovens, television remote controls, wi-fi routers, and automatic thermostats. Similarly, automobiles employ embedded processors to control fuel injectors, antilock brakes, and other components (FIGURE 5).
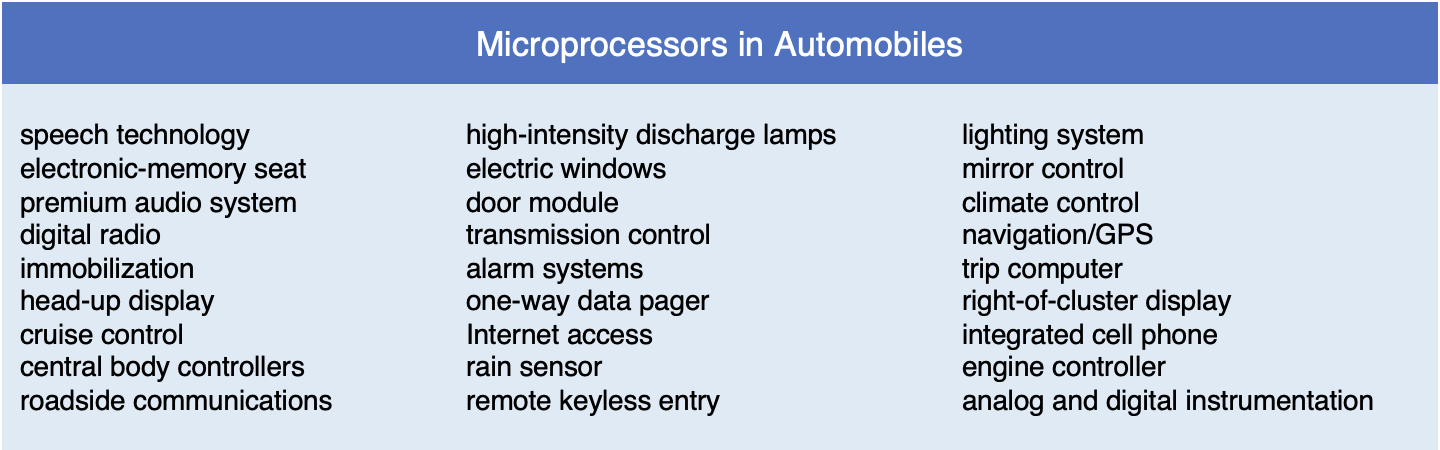
FIGURE 5. Common uses of embedded microprocessors in automobiles.
Society has also been affected by the availability commercial software that enables individuals to accomplish tasks previously reserved for highly trained professionals. For example, word processing and desktop publishing software have made it simple for anyone to produce professional-looking documents, such as reports, newsletters, and flyers. Similarly, most personal computers now come with video-editing software, which enables users to create, edit, and augment digital video images on their computers. In addition, software companies market specialized applications that capture human expertise and make it available to users. For example, tax preparation programs such as H&R Block Taxes integrate graphics, sound, and video to guide users through the process of completing various tax forms (FIGURE 6, left). Online tools such as OpenAI's ChatGPT use advanced artificial intelligence techniques to assist users in writing and creating (FIGURE 6, right). Many of these software applications that capture human expertise are now available as Internet-based services. By offering access to such services over the Web on a pay-per-use basis, software companies can drastically reduce the cost to users while ensuring that all included information is regularly updated.
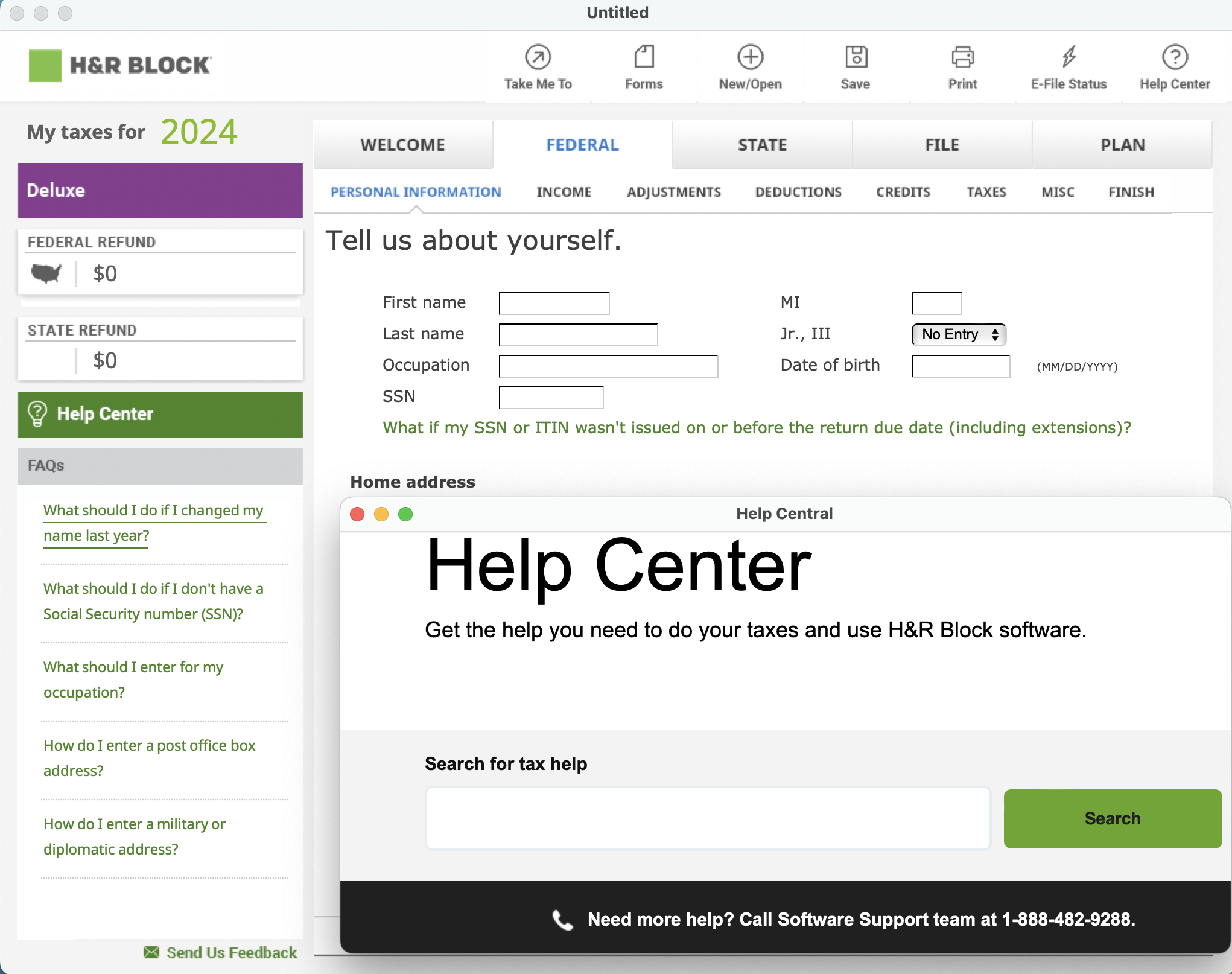

FIGURE 4. H&R Block Tax Software; OpenAI's ChatGPT.
In recent years, new technologies have led to new categories of software. Smart phones and tablets such as the Apple iPad and Samsung Galaxy Tab have driven the development of mobile applications (or apps) that run on these devices. In November 2025, Apple's online App Store offered more than 2 million apps for the iPhone and iPad, while Google's Play Store offered 2.6 million apps for Android devices. Digital readers such as Amazon's Kindle and Sony's Reader allow users to download books and read them on small, portable displays.
✔ QUICK-CHECK 11.4: TRUE or FALSE? Embedded processors are computer chips that are placed inside other processors to achieve faster computation.
Reliance on Complex Systems
As society becomes dependent on complex, computer-based products and services, the effects of computer errors or system failures become far-reaching. Whereas errors in the Web pages you create in this book might cause you frustration or earn you a bad grade in an assignment, errors in software for air traffic control, electrical power relays, and banking systems can endanger lives and cost companies millions of dollars. The following list describes scenarios in which software errors produced dire and unexpected consequences.
- Between 1985 and 1987, six cancer patients received massive radiation overdoses when a Therac25 radiation therapy machine malfunctioned. These malfunctions were eventually traced to a single coding error in the control mechanism for the machine. Four of the accidents resulted in patient deaths, whereas the other two resulted in disfigurement and disability.
- In 1991, 28 soldiers were killed when a Scud missile struck a U.S. Army barracks near Dharan, Saudi Arabia. It was later determined that a Patriot missile battery failed to track and intercept the incoming Scud missile because of a software error. The control software for the Patriot missiles performed a repeated computation involving a non-terminating fraction. The resulting round-off error, when compounded over 100 hours of active use, amounted to a significant timing error that caused the missile to miss its target.
- In 1999, NASA's Mars Climate Orbiter went off course and was destroyed in the Martian atmosphere. The navigational error that caused the crash was traced to inconsistencies in the software-development process at NASA. Apparently, some development teams on the project designed code using Imperial units (e.g., miles), whereas other teams used metric units (e.g., kilometers). No one working on the project noticed this inconsistency, and the required unit conversions were never made. The cost of the Orbiter was $125 million.
- In 2012, the Knight Capital Group lost $461 million in thirty minutes due to errors in its stock trading software. The malfunctioning software mistakenly placed thousands of stock orders simultaneously, instead of spaced out over days, inflating prices and causing panic buying on the market.
- The first death caused by self-driving cars took place in 2018, when a pedestrian in Tempe, Arizona was struck by a self-driving Uber vehicle. Investigations identified a failure of the software control system to recognize the pedestrian and react accordingly. Since then, there have also been 83 fatalities in the U.S. involving self-driving cars (National Highway Traffic Safety Administration).
To avoid errors such as these, the software industry employs design and testing methodologies aimed at minimizing costs while improving the quality of large applications. However, as the size and complexity of software grows, design and testing become significantly more difficult. For example, it might be feasible for an experienced programmer to carefully study a 1,000-line program and ensure that it behaves as expected. However, performing the same type of analysis on a 10,000-line program would require significantly more than 10 times as much work, because each section of code must be tested not only in isolation, but also in relation to the other sections of code. As more software components are added to a system, the number of potential interactions between them grows exponentially. Software bugs are inevitable when the scale of a project makes it too complex for detailed study. For example, when Windows 2000 was released, the operating system was known to contain more than 63,000 bugs in its 35 million lines of code. However, these bugs were not considered critical, as most were extremely unlikely to occur in everyday use and, at worst, required the user to reboot the computer. Clearly, critical systems — such as those that control aircraft or financial networks — necessitate more careful testing and debugging to protect human lives and property.
✔ QUICK-CHECK 11.5: TRUE or FALSE? Commercial software is thoroughly tested so that it is error-free when released.
The Internet/Web for Information
With the growth of the Internet, online resources have replaced many traditional sources of information. Unlike print media such as newspapers and magazines, Web sites can be updated 24 hours a day, allowing online publishers to report stories as soon as they break. News sites can also integrate text and pictures with other types of media, such as video footage and interactive polls. Most print and broadcast media offer Web sites, such as the New York Times (nytimes.com), CNN (cnn.com), and Fox News (foxnews.com). Each provides its own perspective on the news and may target different audiences (FIGURE 5).

FIGURE 5. CNN.com and FoxNews.com sites (November 29, 2025).
As social media platforms have grown, many people are using social media sites such as Facebook and Instragram to access news. According to the Pew Research Center, more than 50% of Americans get their news from various social media outlets, with Facebook (38%), YouTube (35%). Instagram (20%) and TikTok (20%) being the most popular. In addition to being convenient and current, online news can be accessed anywhere in the world where the Internet is accessible. Many of the most oppressive governments, e.g., North Korea, China, and Libya, control their internal media in order to limit their citizens' access to news. While they may try to restrict access to online news, this is much harder as technical workarounds are known. In fact, the Arab Spring, a series of pro-democracy protests and uprising across the Arab world in the early 2010s, was directly aided by social media and online news.
✔ QUICK-CHECK 11.6: TRUE or FALSE? More than 50% of Americans get their news from social media outlets.
Fake News & Information Overload
Unlike traditional media sources, which have editors and reviewers to ensure at least some degree of accuracy and impartiality, the Web is neither monitored nor censored. Many Web sites have been created by people or organizations with specific agendas. A company might sponsor Web sites that are favorable to their products. A politician might create a site that mischaracterizes the views of their opponent. An individual might post claims of great accomplishments or use a Web site to denigrate others. The last decade has seen the rise of Web sites specializing in fake news, false or misleading information that is presented as objective news. These sites may appear legitimate but only present skewed information to support a particular political or social viewpoint. With so many news sources available, the danger is that individuals focus on sources that cater to their preexisting biases, creating an "echo chamber" where they only hear news that supports their viewpoint. This has led to an unprecedented level of partisanship and animosity between groups of people, who not only disagree on how to solve problems but also on what the basic facts are. In a 2025 global survey by the Pew Research Foundation, a media of 72% of adults viewed fake news as a major threat to their country (FIGURE 6).
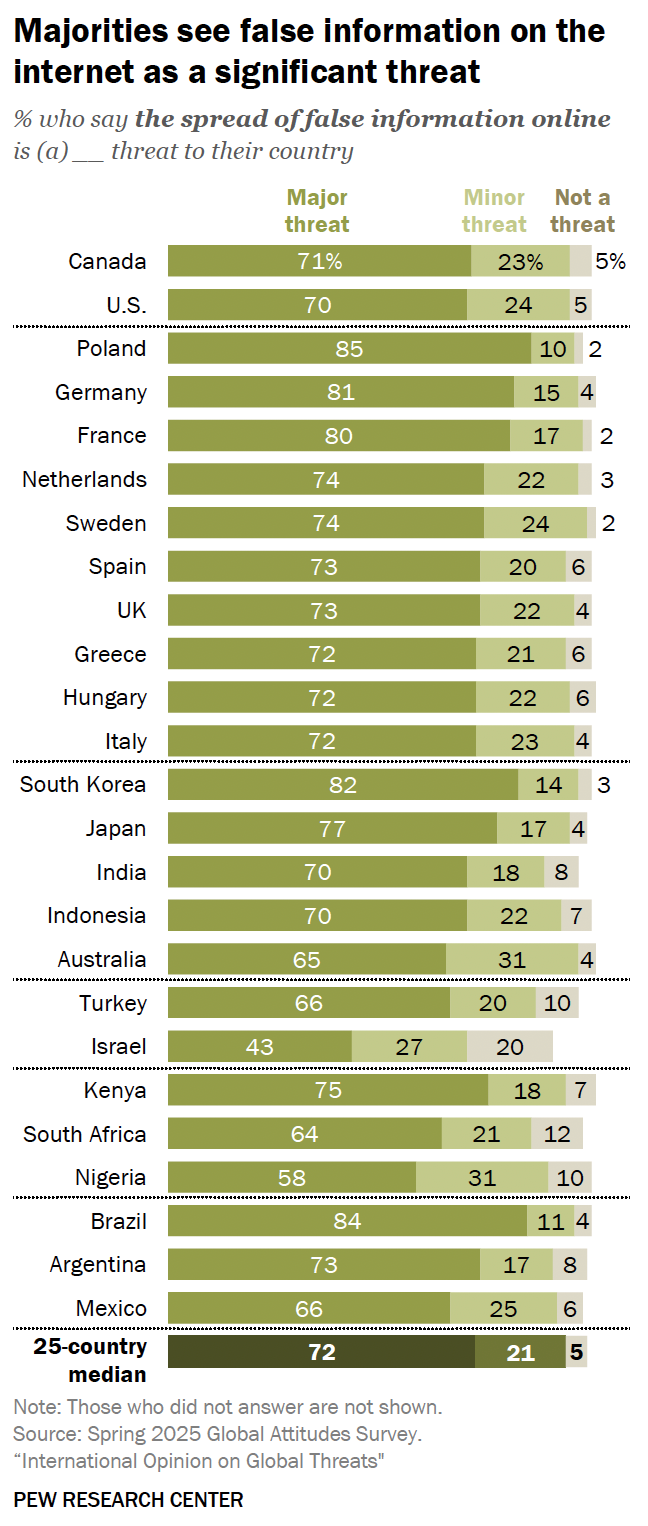
FIGURE 6. Global Survey on Fake News (Pew Research Foundation, 2025).
Because anyone can be a Web author, there is always a chance that the author is uninformed, misinformed, or biased. Moreover, while professional writers are familiar with the idea that complex questions require complex answers, untrained Web authors may settle for short answers that, although not entirely inaccurate, lack context and justification. For example, a Web search on the simple question "What is the capital of Missouri?" returns numerous pages that provide the correct answer: Jefferson City. However, entering a more complex question such as "Who invented the computer?" produces pages with a variety of answers, including Alan Turing, Konrad Zuse, Charles Babbage, John Atanasoff, and John von Neumann. As we learned in Chapter C4, each of these figures contributed to the development of computing technology in a different way. Responsible researchers would need to explain these answers in context to justify them. FIGURE 7 lists several criteria that can be applied to online content to evaluate its credibility.

FIGURE 7. Criteria for evaluating online content.
Although the impressive breadth of information available online can be viewed as a positive, it is also one of the medium's greatest negatives. The fact that individuals can add content to the Web ensures that all ideas and perspectives can be heard. Unfortunately, the massive volume of data created by the online community isn't particularly organized, which makes finding any single piece of information difficult. Various sources have estimated the current size of the Web in the hundreds of trillions of pages. To help navigate this vast sea of information, search engines such as Google and DuckDuckGo automatically catalog Web pages and allow users to search for data by topic or keywords (see Chapter C2 for more details). Google is by far the most popular search engine, processing more than 100,000 search queries per second (InternetLiveStats.com). It is important to note that search engine results must always be viewed critically. Companies that advertise with the search engine company are often given preferential placement on the search results page. In addition, there are techniques that Web developers can use to artificially inflate their ranking in the search results. Thus, when conducting research using a search engine, the user needs to look carefully at the source of the information and seek independent, corroborating sources when accuracy is essential.
✔ QUICK-CHECK 11.7: TRUE or FALSE? The results provided by a search engine are verified to be correct.
The Internet/Web for Communication
As we saw in Chapter C3, the exponential growth of the Internet during the 1980s was fueled in part by a proliferation of communications-based applications. Countless scientists, government workers and university researchers were drawn to the Internet by the availability of electronic mail and newsgroups. When Internet access became more widespread in the 1990s, a broad group of nontechnical users began going online to exchange business and personal information. In 2025, there were an estimated 4.5 billion active email users worldwide, with 40% (1.8 billion) using Google's Gmail. An average of 376.6 billion emails were sent every day, or 4.35 million emails per second. Unfortunately, approximately half of those emails were spam, unsolicited messages advertising some product or service (Statista).
The growth of the Internet and Web as communications media was greatly accelerated by the widespread adoption of mobile devices. In 2025, the Pew Research Center found that 98% of American adults owned a cell phone. Furthermore, more than 91% owned smartphones, enabling them to access the Web and various communication tools directly on their phones. Especially among younger users, text messaging, or texting, has largely replaced phone calls and email as the medium for mobile communication. An estimated 9.1 trillion texts were sent worldwide in 2025, for an average of 105 million texts per second (SellCell). Increased use of convenient mobile devices also spurred the growth of social media sites that combine information/news sources with communications and community building. FIGURE 8 shows the most popular social media platforms, broken down by age groups. The largest platform, Facebook, reported more than 3 billion users in 2025.
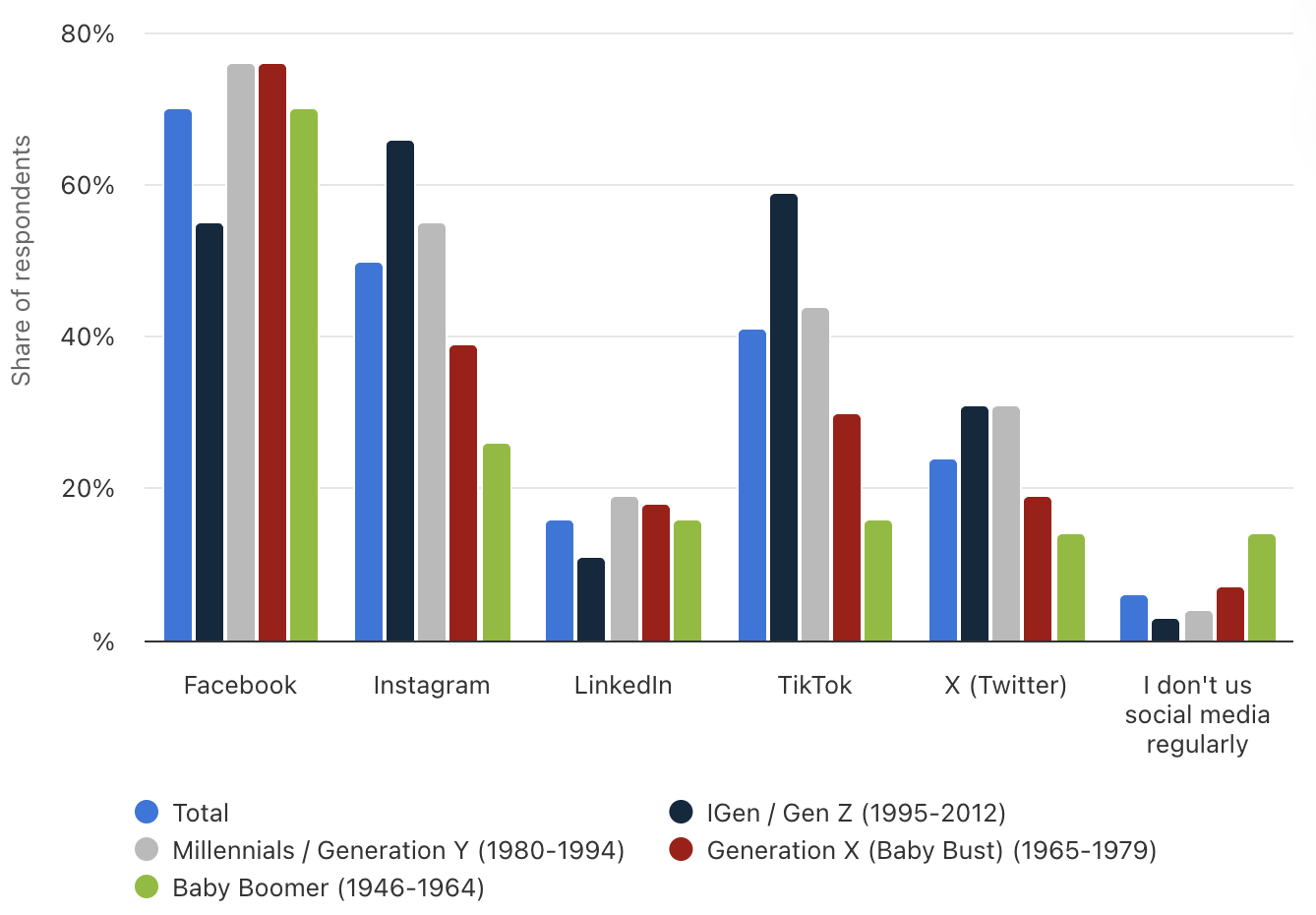
FIGURE 8. Social Usage by Age Groups (Statista, 2025).
✔ QUICK-CHECK 11.8: TRUE or FALSE? Approximately half of all email messages are spam.
Addiction & Cyberbullying
The convenience of mobile devices and the connectivity people feel via texting and social media also have a dark side. In 2025, the average adult spent more than 7 hours a day on their connected devices (Statista). Since American adults average 7 hours of sleep per night, this implies that they were spending 7 out of the remaining 17 hours (or 41% of their waking day) on their devices. Those are hours that the person could be engaging in healthier activities, such as reading, experiencing nature, exercising, or building relationships.
Medical studies have shown that the texting and social media use can be both physically and psychologically addictive. Positive feedback on social media (e.g., likes or retweets) produce chemical reactions in the brain similar to those derived from drugs like cocaine. The fear of being detached from mobile phone connectivity is now commonly referred to as nomophobia (as in "the fear of no mobile phone"). Nomophobia is not yet officially recognized as a mental disorder by health organizations, but the phenomenon of social media users exhibiting anxiety when disconnected is well documented.
As children turn more and more to social media, negative social interactions move there as well. Bullying and harassment through texting and social media, known as cyberbullying, is a serious issue for pre-teens and teens. According to a survey by the Cyberbullying Research Center, 54% of female teens and 36% of male teens experienced online harassments in 2025. FIGURE 9 shows a range of issues that respondents reported as a result of experiencing cyberbullying. These numbers are troubling, especially the statistic that 26% of bullied youths had suicidal thoughts. This connection has been made by other studies, including one that showed the suicide rate for teen girls increased by 65% between 2010 and 2015, coinciding with the rise in smartphone social media use among teens (Science Daily).

FIGURE 9. Emotional and Behavioral Impact of Cyberbullying (SQ Magazine, 2025).
Obsessive use of smartphones can lead to other unsafe behaviors. According to the National Highway Traffic Safety Administration, texting while driving is 6 times more dangerous than intoxicated driving. In 2023, more than 1.6 million crashes were caused by drivers using cell phones and texting.
✔ QUICK-CHECK 11.9: TRUE or FALSE? Cyberbullying is a serious problem, especially among preteens and teens.
The Internet/Web for Commerce
Another popular function of the Web is to facilitate electronic commerce, or e-commerce. Online shopping offers numerous benefits to consumers. Instead of searching through the mall and standing in long lines, shoppers can make purchases from the comfort of their homes at any time of day or night. Web-based commerce also makes it easier to comparison shop, i.e., compare the products, features, and prices offered by various companies. Furthermore, online stores provide more detailed product descriptions and reviews than would be available through conventional stores, which helps consumers make more informed purchasing decisions. Many of the largest e-commerce sites are online offshoots of traditional retailers, such as www.walmart.com, www.bestbuy.com, and www.petsmart.com. In addition, many banks and retailers provide online services such as account tracking and online bill payments for the convenience of their customers.
Although some companies use the Internet to complement their traditional sales and services, others are strictly online ventures. The largest e-commerce site in terms of yearly sales, Amazon.com, is a strictly online company that was founded by Jeff Bezos in 1994. According to the U.S. Census Bureau, online sales for the U.S. e-commerce sector exceeded $1.2 trillion in 2025, which is more than 21% of the total economy. Amazon.com accounted for 37.6% of that number (FIGURE 10).
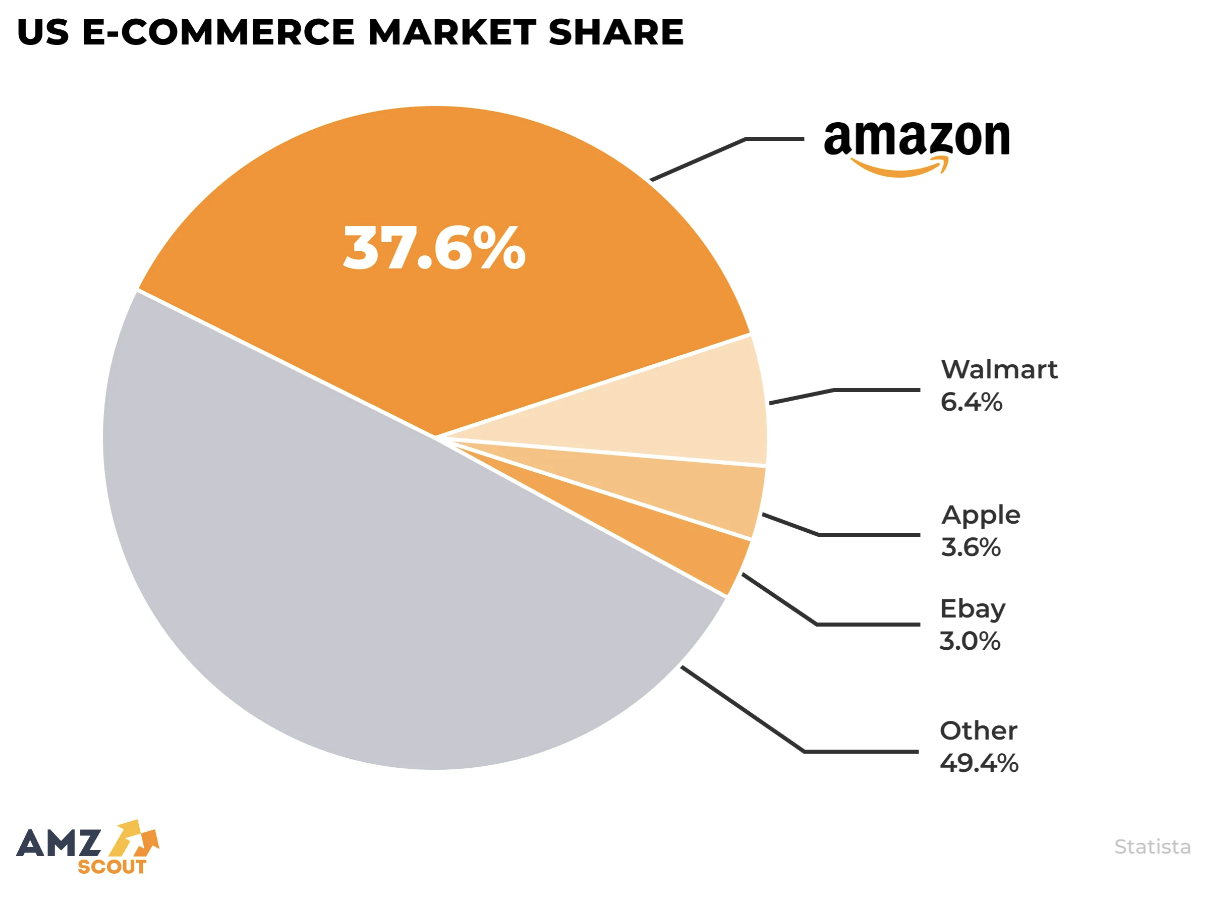
FIGURE 10. U.S. E-commerce Market Share.
The Internet and Web have provided new advertising channels for businesses and organizations. The most common method of Internet-based advertising involves the owners of popular Web sites charging fees in exchange for hosting advertising banners on their pages. These so-called banner ads are clickable images that promote a particular company's product or service. Users who click an ad are typically directed to the company's Web site, where they can make purchases or review additional product-related information. Some marketers have turned to more aggressive means of capturing the consumer's attention, such as animated, interactive ads or pop-up ads that open a new window that the user must manually close. To help combat intrusive advertising, modern browsers incorporate a variety of tools, including pop-up window blockers and fraudulent Website registries. From a publicity perspective, Internet-based advertising offers potential advantages over other, more traditional channels, as the Web's structure makes targeted marketing easier and allows direct connections between ads and related purchasing interfaces.
In addition to facilitating business-to-consumer (B2C) transactions, the Internet is widely used for communication and information exchanges within and among businesses. Business-to-business (B2B) transactions allow companies to manage inventory more dynamically, improve efficiency by linking various data channels, and form partnerships based on sharing resources and information.
✔ QUICK-CHECK 11.10: TRUE or FALSE? Walmart.com is the largest e-commerce site in terms of online sales.
Privacy
When using credit cards or shopping online, consumers often sacrifice their privacy for the sake of convenience. Most credit card companies and online retailers maintain detailed records of customer purchases to identify patterns and predict future sales. Although such records can be used to improve customer service, there is significant potential for misuse. By analyzing a person's purchasing history, a company can infer many otherwise private details of the person's life, including hobbies, travel patterns, and personal contacts. For example, a 2012 story made national headlines when a father complained to a large retailer about its marketing of pregnancy products to his teenage daughter, only to discover that she was unknowingly pregnant (which the retailer had inferred from her purchase history). Compounding the privacy concerns is the fact that companies commonly sell customer profiles to marketing firms and other retailers, which makes it virtually impossible for consumers to control or even know who has access to their data. Web users can at least attempt to limit the exploitation of their personal data by interacting only with reputable online businesses. Most such companies have established privacy policies outlining the ways in which they handle customer information, and many explicitly promise not to sell data to third parties. To ensure that companies follow their own privacy policies, third-party organizations such as TRUSTe.com have been formed that evaluate companies' privacy procedures and offer accreditation seals.
Email also raises privacy concerns in our technology-driven society. As email messages travel across the Internet, they pass through numerous routers that direct the messages to their destinations. Each router represents a security risk, because someone could gain access to the router and eavesdrop on messages that are relayed. When an email message is received, it is commonly stored in a file on the recipient's computer. If that message contains sensitive personal or business information, there is also a danger that unauthorized users might get access to that file. Whereas legislation explicitly protects the privacy of letters and packages sent through the U.S. Postal Service, there are few laws that apply directly to electronic privacy. Furthermore, courts have overwhelmingly favored employers over employees in invasion-of-privacy suits involving email. Unless a company or organization explicitly states its policy on electronic privacy, it may be assumed that the company has the right to access any content on company-owned machines. This has been ruled to include emails written or received by employees, even if the emails are unrelated to company business.
In recent years, a growing threat to user privacy is phishing, the act of obtaining sensitive information (e.g., credit card numbers, usernames, or passwords) by masquerading as a trusted entity in an email. These emails may claim to be banks seeking account confirmation, Internet service providers attempting to verify account information, or lost acquaintances hoping to reconnect. By responding with sensitive information, users are susceptible to financial loss or identity theft. In addition to direct financial losses, email accounts compromised via phishing are commonly used as platforms for spam attacks.
✔ QUICK-CHECK 11.11: TRUE or FALSE? Phishing is a marketing technique in which a commercial site offers deals to entice customers.
Chapter Summary
- Computers and the Internet have changed the ways in which people carry out daily tasks, access information, communicate with each other, and conduct business.
- The development of transaction processing devices and networking in the 1980s led to the increased use of electronic money (via credit/debit cards and automated teller machines).
- A cryptocurrency is an electronic form of money whose value is entirely determined by the free market. Cryptocurrencies utilize encryption to keep accounts secure and allow for anonymous (and potentially tax-free) transactions.
- Credit card debt is a major concern for many families, with credit card debt often exceeding savings.
- Identity theft and fraud, where criminals steal personal information and pose as that person in order to extract cash or make purchases, is a growing concern as more people rely on credit cards and online shopping.
- Embedded processors, computer chips that are built into appliances and machinery to control their workings, account for more than 98% of all computer processors.
- As society becomes dependent on complex, computer-based products and services, the effects of computer errors or system failures become far-reaching (e.g., failure of medical machinery controls can lead to patient deaths, bugs in switching software can lead to telephone network outages).
- The Internet and World Wide Web provide alternative sources of news and information that can be updated easily and accessed by people worldwide.
- Because the Web is large and there are few controls on the quality of page content, finding desired information on the Web and verifying its authenticity can be difficult.
- Criteria that can be applied to online content to evaluate its credibility include author reputation, author objectivity, content review, content verifiability, and content timeliness.
- The growth of the Internet and Web as communications media was greatly accelerated by the widespread adoption of mobile devices, texting and social media.
- The fear of being detached from mobile phone and social media connectivity has been termed "nomophobia." Cyberbullying and texting while driving are two other negative effects of mobile phone addiction.
- Online shopping can be more convenient for consumers, and it makes product research and comparison shopping easier.
- Banner ads are clickable images that promote a particular company's product or service.
- Online activities raise privacy issues as companies store individual activities and preferences. Most reputable companies establish privacy policies outlining the way in which they handle customer information and use encryption techniques to protect private information as it is transmitted.
Review Questions
- In addition to the examples listed in this chapter, describe two other aspects of society that have been greatly impacted by computer technology. Within these areas, what specific activities or jobs were most affected? Overall, has the impact been positive or negative? Justify your answers.
- In an average week, how many cash purchases do you make? How many debit or credit card purchases? Do you have any anxiety about the amount of information banks and credit card companies collect from your purchase history?
- Use the Web to determine the current dollar value of a bitcoin. How stable has its value been (e.g., did it change substantially in the past week or month)?
- Describe one advantage of specialized applications such as tax preparation software. Describe one potential disadvantage.
- Use the Web to identify a recent (within the last year) incident where a computer or software failure resulted in significant loss of money or lives. Was the cause of failure identified and fixed?
- Describe two advantages of online newspapers over their print counterparts. Do you think that electronic newspapers will completely replace printed papers in the near future? Why or why not?
- Perform a Web search on your name. That is, enter your name into a search engine, such as Google or DuckDuckGo, and then search the Web for occurrences of that name. How many matching pages did the search engine find? If you have your own Web page, did the search engine find it? You may need to include additional search parameters if your name is relatively common.
- If you own a smartphone, how many different apps do you use regularly? If not, what factors led to that choice (e.g., cost, personal preference, privacy concerns).
- Most smartphones track your screen time and provide a report each day or week. If you own a smartphone, access this feature and report how many hours a day (on average) that you spend on your phone. If you do not own a smartphone, log your online activities in a 24-hour period and report the number of hours you spent online.
- Describe two advantages of online shopping over in-person retail outlets. Do you personally prefer making purchases online versus going to stores? Explain your reasoning.
